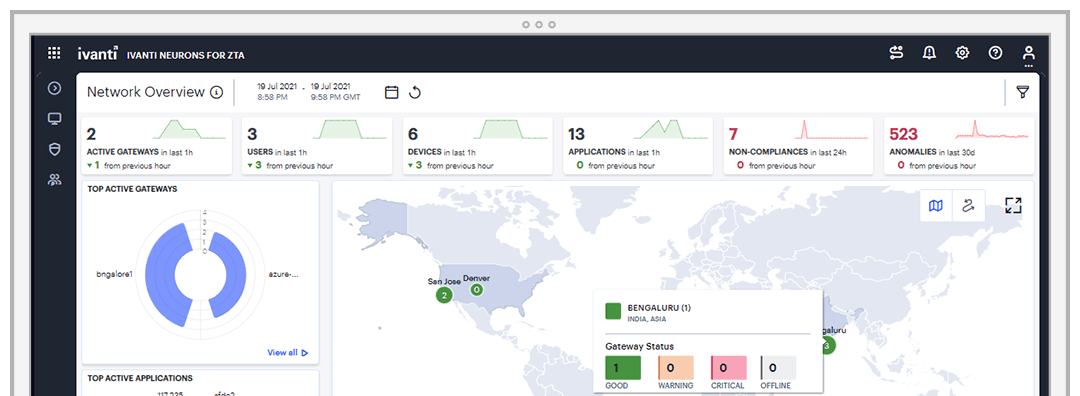
Ivanti Neurons for Zero Trust Access empowers organisations to adopt a security model built on continuous verification and least privilege access. By dynamically assessing user identities, device posture and application access, Ivanti Neurons for Zero Trust Access enforces granular access controls, granting authorised users access to only the resources they need. Step into the future of security with the confidence of Zero Trust, empowering your workforce in a borderless digital landscape.
Unified access
Leverage a unified client to streamline and simplify the management of access solutions. Experience seamless integration for VPN, software gateways and secure access, all within one comprehensive platform.