Have confidence knowing that your business is protected with continuous threat management and secure access across every user, device, application and network—anywhere, anytime.
IT Security Solutions
A Secure IT Estate Powers Everywhere Work
Ensure peace of mind, everywhere your business works
Get tough and smart about security
What if you could deploy and maintain the highest level of security across your infrastructure, from cloud to edge, identifying and heading off threats before they can disrupt service? We make it happen, with comprehensive patch management and zero trust security solutions that leave zero room for compromise.

Maximise your confidence
Protect your organisation against an ever-evolving threat landscape. Ivanti’s multi-layered security solution creates a nearly unbreachable fortress against ransomware, phishing, vulnerabilities, and other cyber threats at the user, device, network, and application levels.
Design and deploy zero trust security and protect your business everywhere it works— from the data centre to the cloud to the edge
Step into the future of secure mobility
Secure your mobile workforce with passwordless sign-on and zero-trust access, and ensure seamless, secure experiences everywhere.
Secure your workplace everywhere
Ivanti’s simple, automated solution empowers you to quickly and proactively identify, update and patch cyber threats across your extended environment.
Discover it. Secure it.
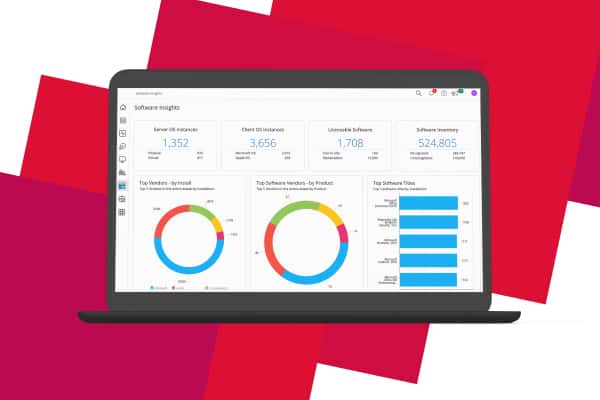
Real-time visibility of your IT landscape lets you secure every device and asset continuously from one dashboard.
Get started
If you want to learn more about how Ivanti’s security solutions automatically protect your users everywhere, let’s connect.



